In the first part of this series, we went over the most of ipsw commands and today we will continue with the rest of them. We will see how to work with kernelcache, img4, how to interact with the USB connected device and more.
extract
We will start with the ipsw extract command which allows us to extract kernelcache, dyld_shared_cache, DeviceTree and Im4p keybags from IPSW/OTA files.
Since we have already covered extracting DeviceTree, we will jump right into dumping kernelcache and dyld_shared_cache. kernelcache is basically a kernel along with all the extensions (kexts). To actually analyze the kernelcache, we first need to extract it. We will later see how to analyze and get some interesting information out of it.
command: ipsw extract --kernel PATH_TO_IPSW_FILE

To dump the dyld_shared_cache, we pass the --dyld flag instead of --kernel.
command: ipsw extract --dyld PATH_TO_IPSW_FILE

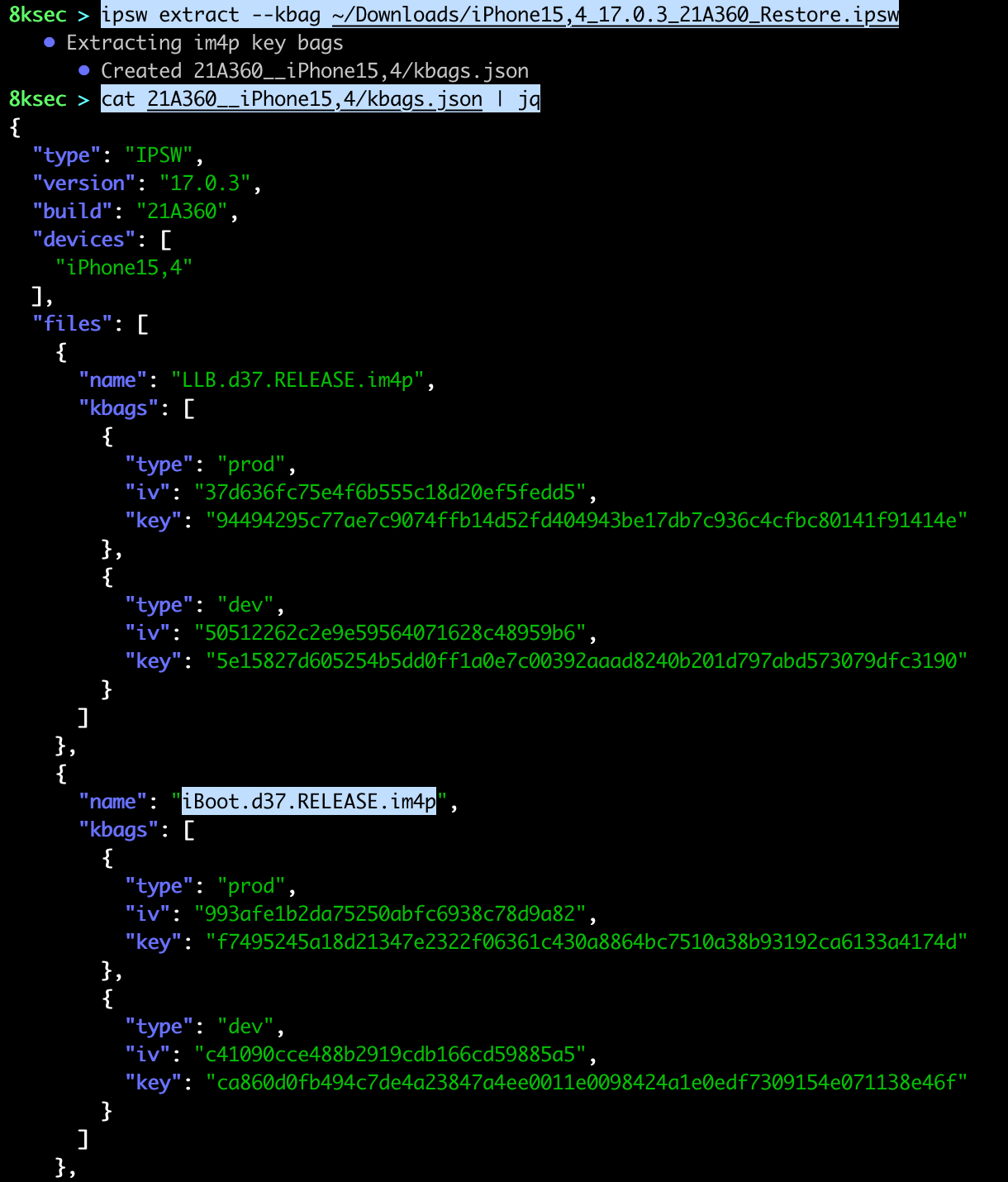
Another useful feature is dumping im4p keybags as json file. im4p file is a payload of IMG4 file format which is used for iBoot, ramdisk etc for 64 bit devices.
command: ipsw extract --kbag PATH_TO_IPSW_FILE
idev
ipsw idev provides a lot of functionality related to the interaction with the USB connected device.
afc
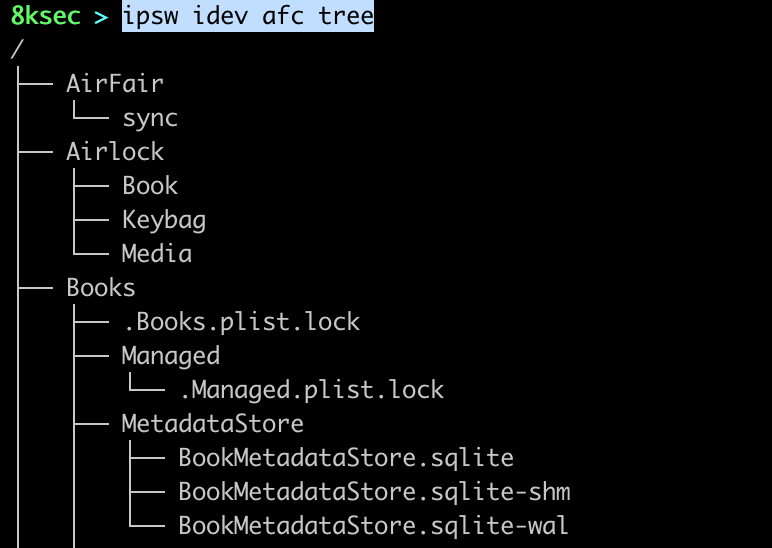
The first ipsw idev subcommand is afc which provides a couple of filesystem commands which allows us to manipulate files and directories inside of /var/mobile/Media on the device.
command to list files: ipsw idev afc ls OPTIONAL_FILE

command to list all files: ipsw idev afc tree
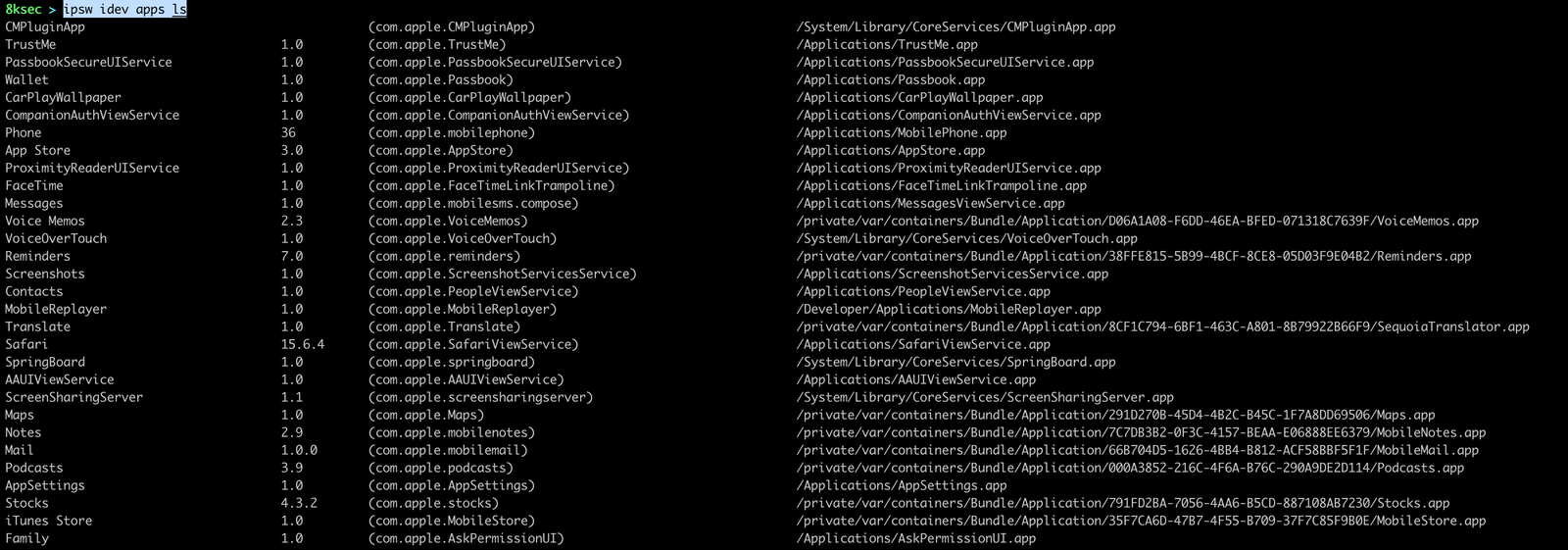
apps
ipsw idev apps command allows us to view installed application, install the application from IPA file or uninstall them.
command_to_list_apps: ipsw idev apps ls
command_to_uninstall_app: ipsw idev apps uninstall BUNDLE_ID

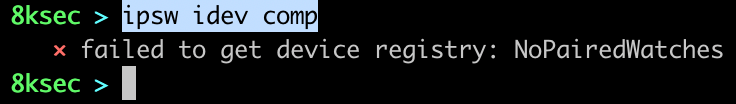
comp
ipsw idev comp allows us to view all companion paired devices, such as AppleWatch.
command: ipsw idev comp
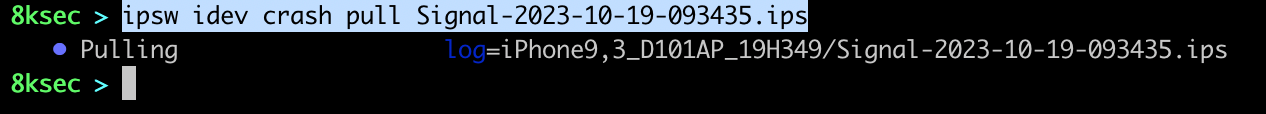
crash
This command gives us an ability to work with crashes. We can list the crashes, clear them all or download them.
command_to_list: ipsw idev crash ls

command_to_download_crash: ipsw idev crash pull NAME_OF_THE_CRASH
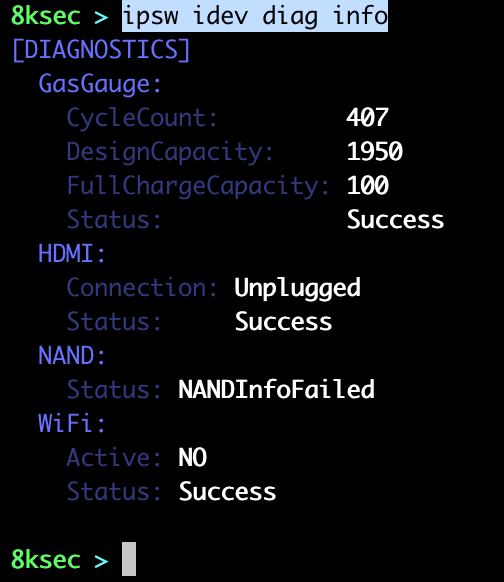
diag
ipsw idev diag provides us with the couple of diagnostics commands, such as getting snapshot of battery data, querying IORegistry, shutting down, rebooting and putting the device to sleep.
command_to_get_info: ipsw idev diag info
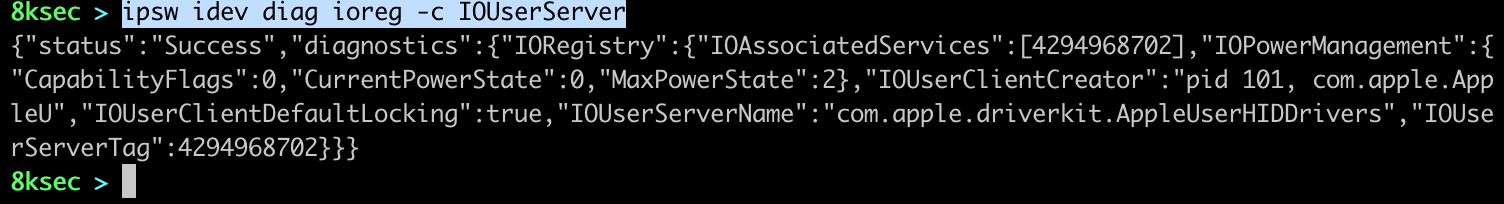
We can also view I/ORegistry which is a dynamic database of which describes a collection of drivers and it has tree structure.
command_to_query_ioreg: ipsw idev ioreg FLAGS
fsyms
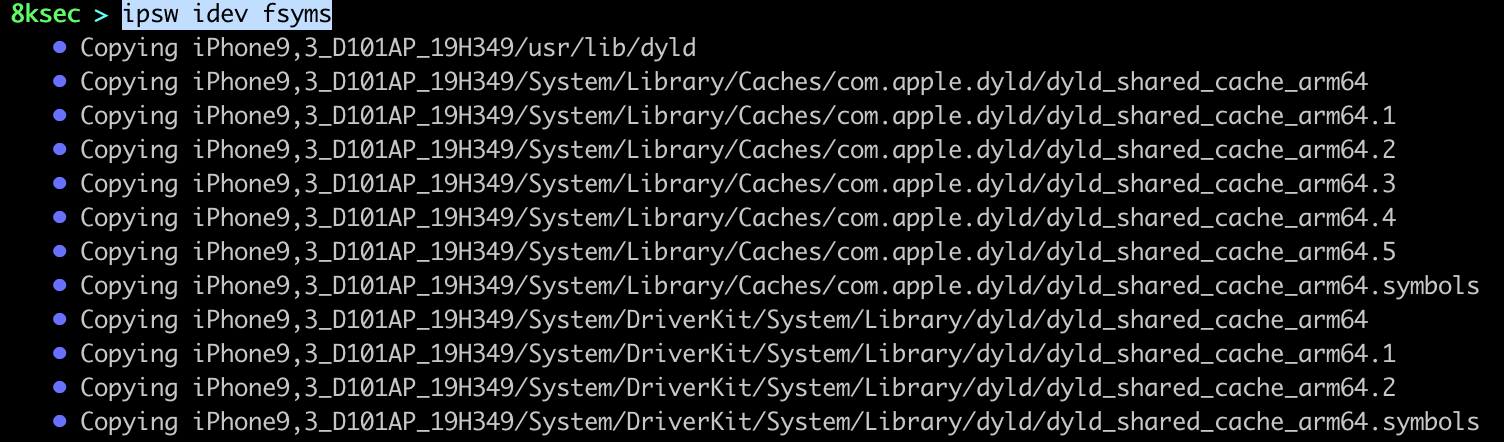
Another useful command which allows us to download linker and dyld_shared_cache from the device, this can come in handy when we want to for example symbolicate the crash.
command: ipsw idev fsyms
list
We can list the information about the connected device using ipsw idev list.
command: ipsw idev list

pcap
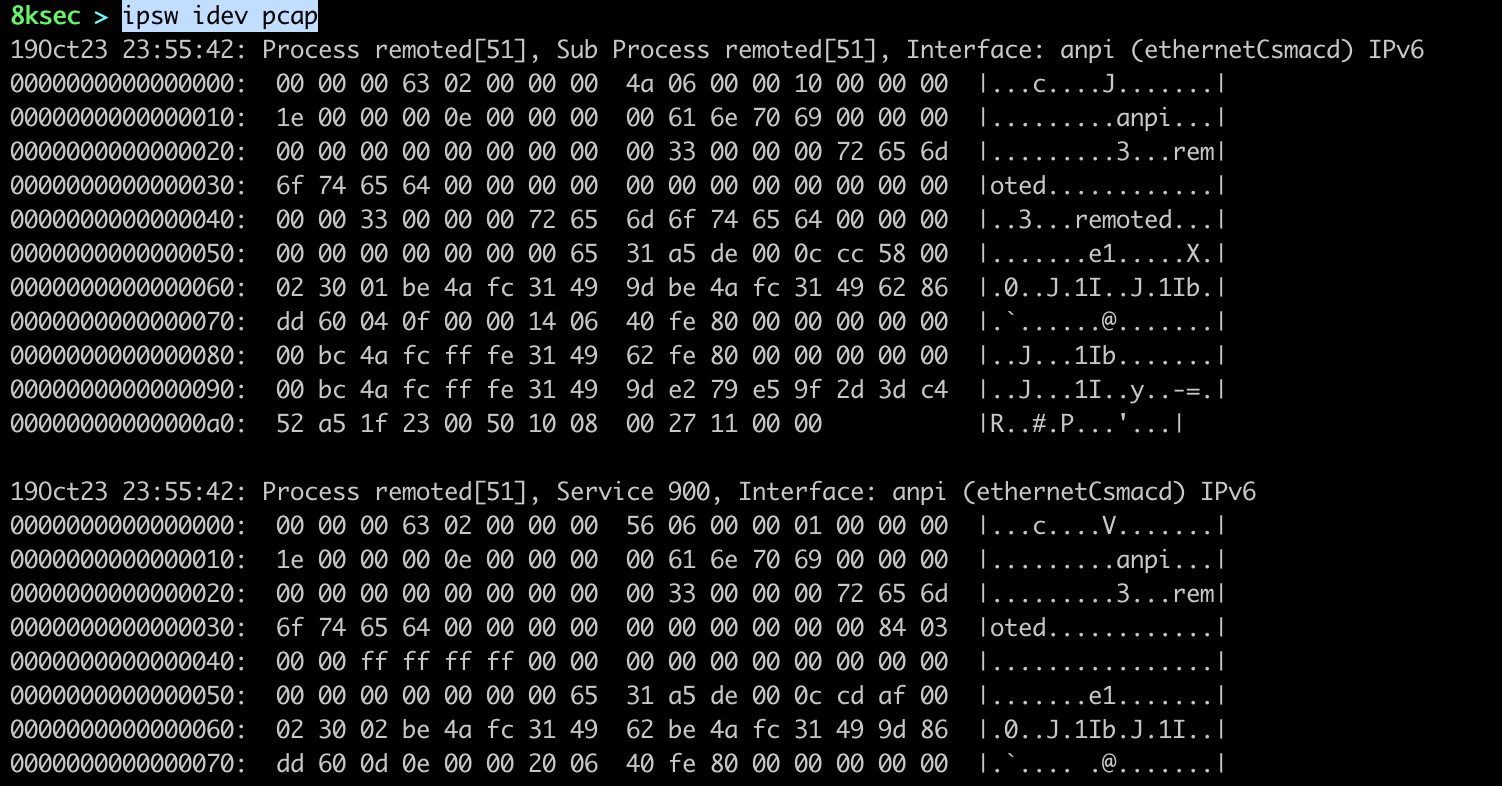
This command allows us to capture the traffic. We can optionally filter it by the process ID.
command: ipsw idev pcap OPTIONAL_FLAGS
proxy
In a situation where we want to proxy the connection from our localhost to port on the USB connected device, we can use this command.
command: ipsw idev proxy --lport LOCAL_PORT --rport REMOTE_PORT

restore
We can enter and exit recovery mode using ipsw idev restore
command_to_enter_recovery: ipsw idev restore enter
command_to_exit_recovery: ipsw idev restore exit
screen
We can take screenshot of the device using ipsw idev screen
command: ipsw idev screen

syslog
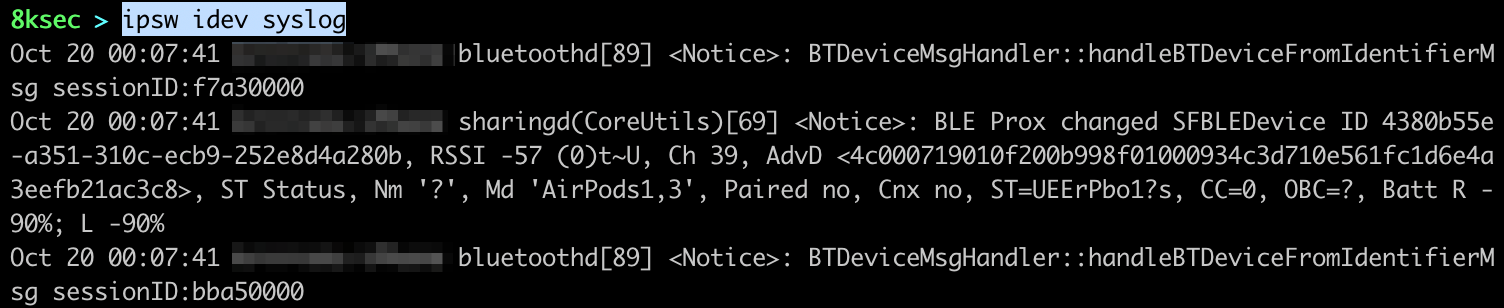
We can monitor the syslog of the connected device using ipsw idev syslog command.
command: ipsw idev syslog
img4
ipsw img4 allows us to work with the im4p files. For example, if we dump the iBoot from the IPSW file using ipsw extract, it will be in the im4p format.

We can see that the extracted files are in im4p format. These files are encrypted and if we want to decrypt them, we first need to extract keybags in order to see the key.
command: ipsw img4 kbag PATH_TO_IM4P_FILE

Once we have obtained the key from the keybags we can now decrypt the im4p file, but before doing that, we can also extract payloads using ipsw img4 extract.
command: ipsw img4 extract PATH_TO_IM4P_FILE
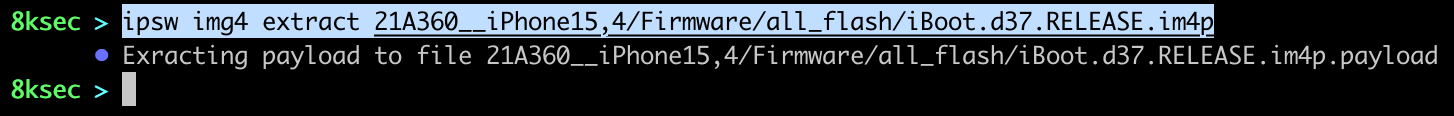
We can see that now we have new file(iBoot.d37.RELEASE.im4p.payload) which is the actual payload/content inside of im4p files.
command: ipsw img4 dec -i IV_FROM_KEYBAGS -k KEY_FROM_KEYBAGS PATH_TO_IM4P_FILE.

kernel
ipsw kernel commands allows us to work with kernelcaches. It supports things such as viewing DWARF debug information, extracting kernel extensions (kexts), viewing syscalls, sandbox operations and more.
ctfdump
ipsw kernel ctfdump allows us to view CTF (Compact ANSI-C Type Format) format which is similar to DWARF format and contains a lot of useful information for reverse engineering. It is worth to note that only KDK (Kernel Development Kit) contains these information.
command: ipsw ctfdump PATH_TO_KDK

dwarf
ipsw kernel dwarf allows us to view DWARF debug information. We need to pass it the type to lookup or we can do diff on types or two kernels.
command: ipsw kernel dwarf --type TYPE_TO_LOOKUP PATH_TO_DSYM

kexts
ipsw kernel kexts allows us to view kernel extensions. Kernel extensions are like module to the kernel and each provides specific functionality.
command: ipsw kernel kexts PATH_TO_KERNEL

extract
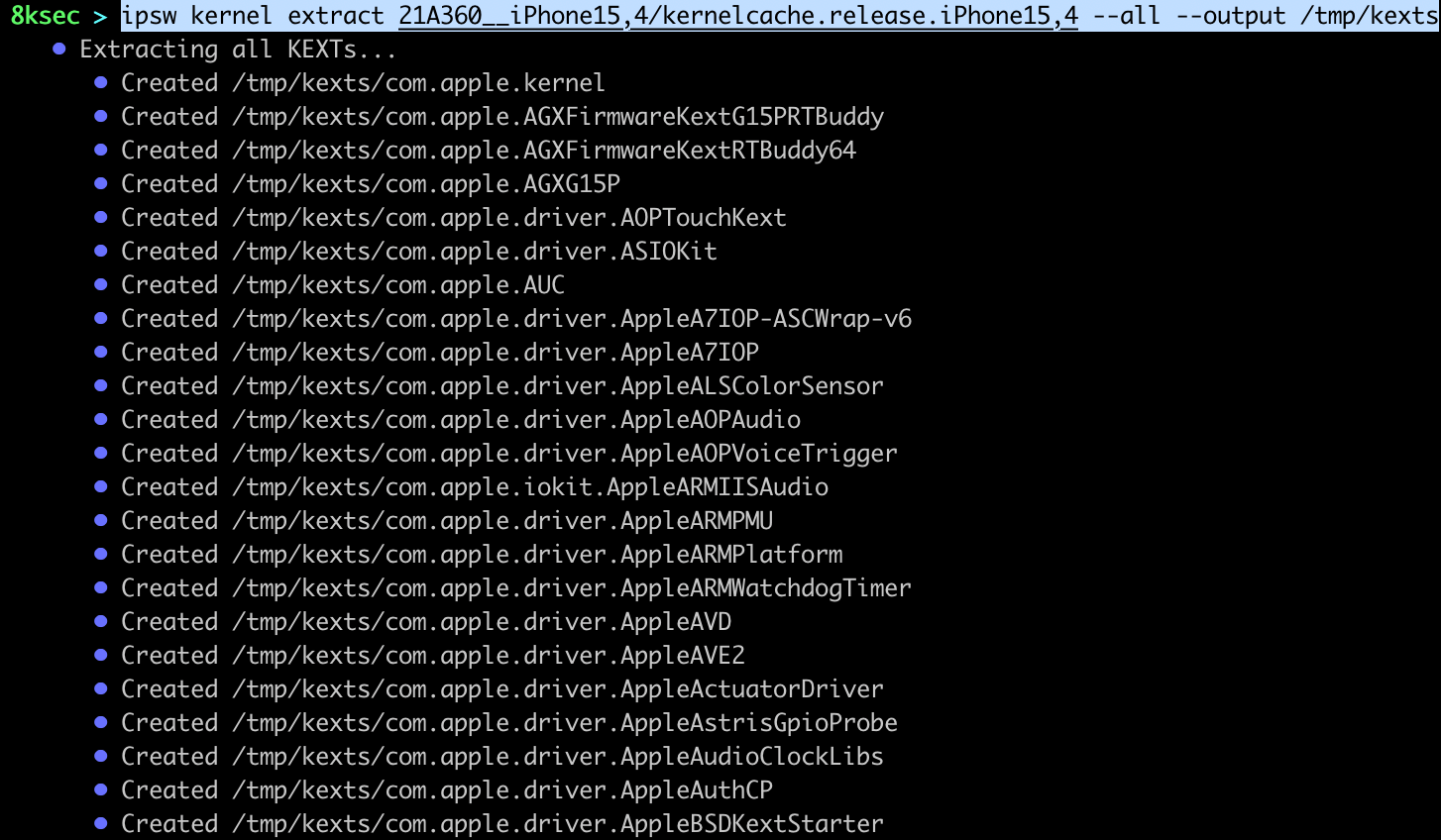
ipsw kernel extract allows us to extract a single or all of the kernel extensions.
command: ipsw kernel extract PATH_TO_KERNELCACHE KEXT
sbopts
We can view sandbox operations using ipsw kernel sbopts.
command: ipsw kernel sbopts PATH_TO_KERNEL

syscall
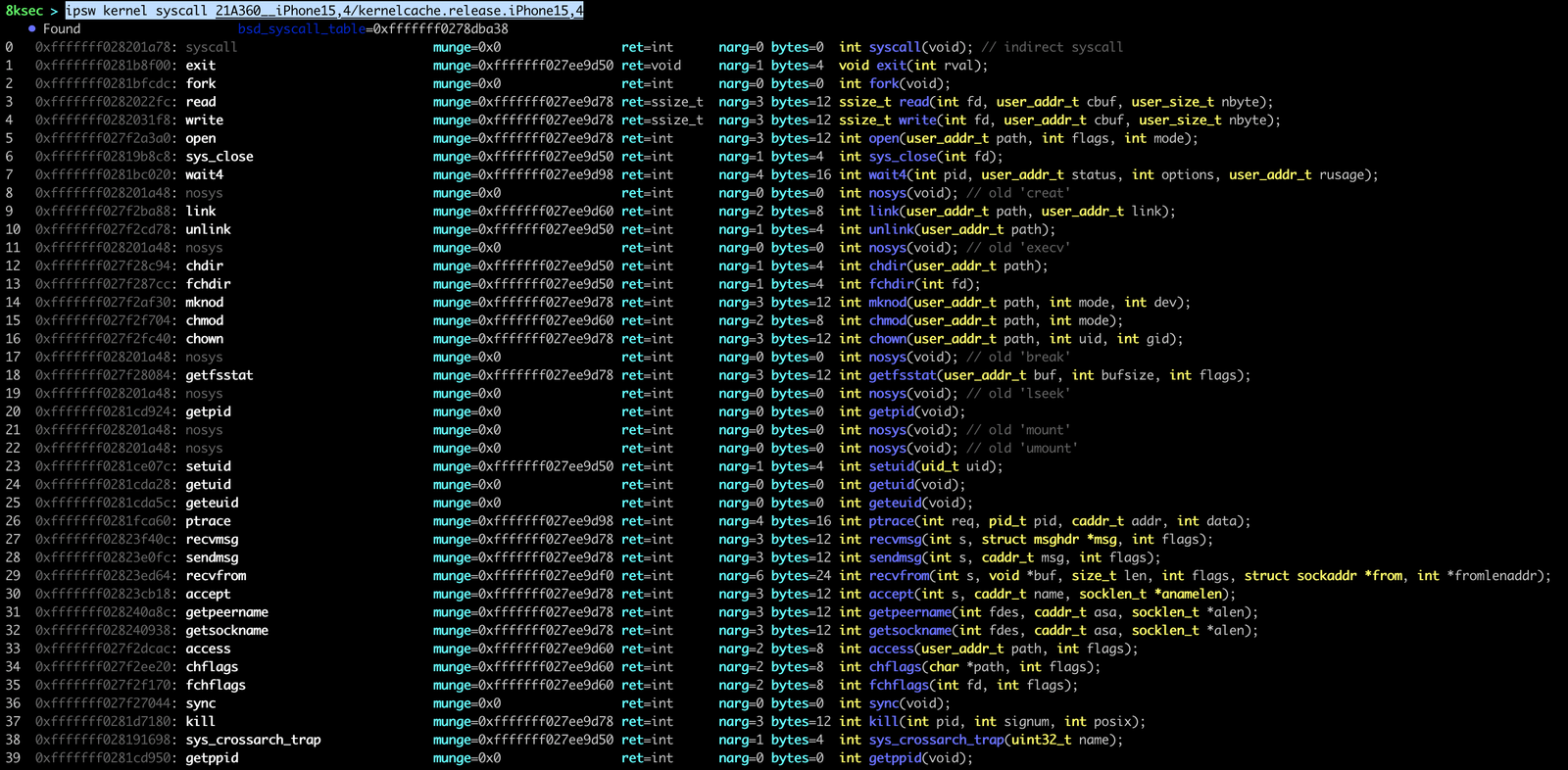
We can view the list of syscalls (system calls) using ipsw kernel syscall.
command: ipsw kernel syscall PATH_TO_KERNEL
ota
ipsw ota allows us to parse OTA (Over-The-Air) files which is file format to update the device using wireless network.
info
ipsw ota info returns as a basic information about the OTA file, such as version, kernelcache, CPU, etc.
command: ipsw ota info PATH_TO_OTA_FILE

extract
Based on the pattern of filename, we can extract the files using ipsw ota extract command.
command: ipsw ota extract PATH_TO_OTA PATTERN

ls
We can view all the files inside of OTA file using ipsw ota ls.
command: ipsw ota ls PATH_TO_OTA_FILE

patch
If we want to work with the versions of iOS of 16.x and greater or macOS of 13.x and greater, we need to patch cryptex volumes. cryptex (CRYPTographically-sealed EXtension) is a mean of deploying updates/patches without updating the entire system and they are the base for the Rapid Security Response.
command: ipsw ota patch PATH_TO_OTA_FILE --output OUTPUT_DIRECTORY
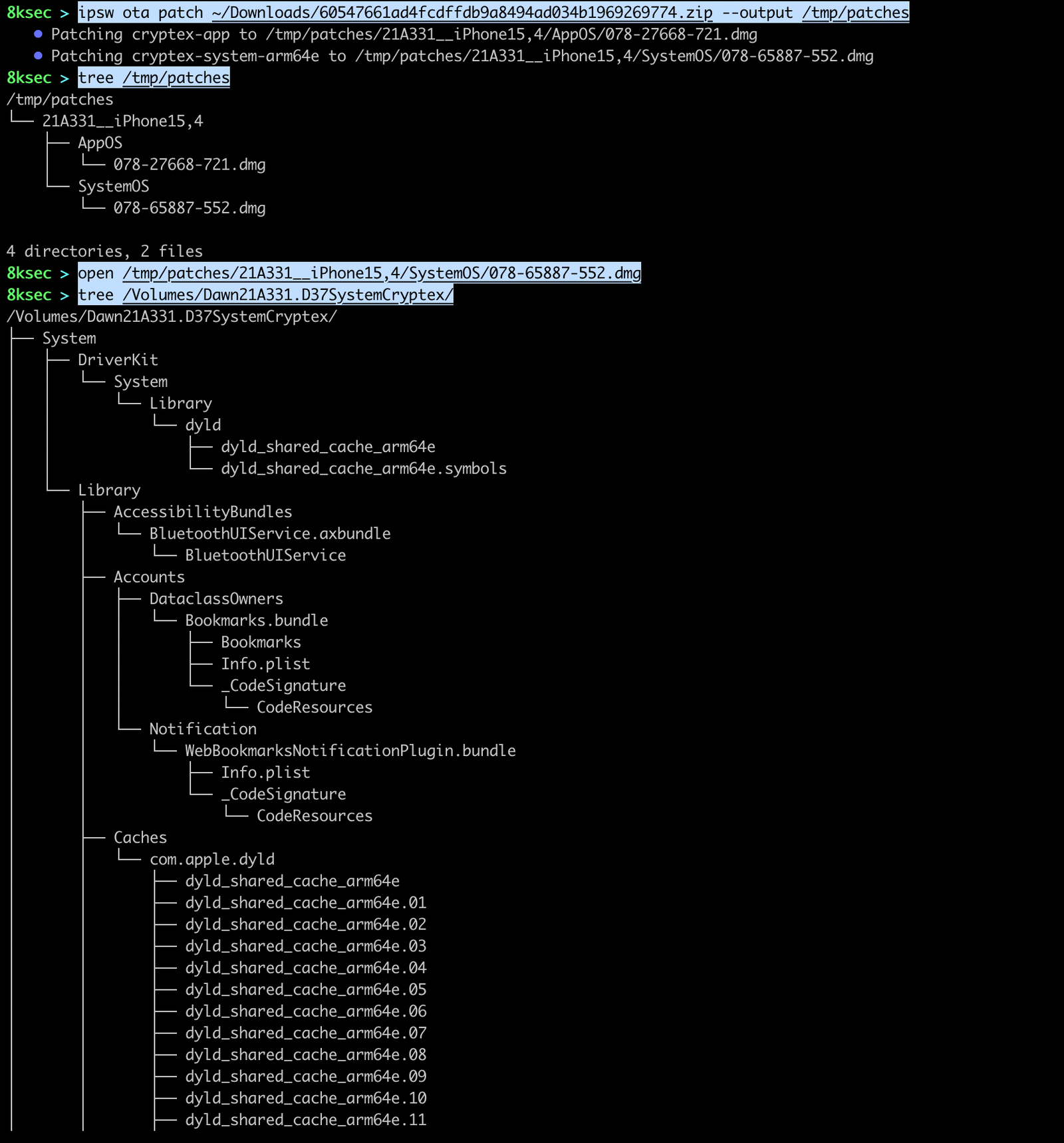
ipsw ota patch can also be used to apply OTA of Rapid Security Response which we can use to diff them. To apply the RSR OTA patch, we first need to extract the patches of previous version and then download the RSR OTA patch followed by the command below. RSR OTA files can be downloaded using ipsw download ota command.
command_to_apply_patch: ipsw ota patch --input PATH_TO_PREVIOUS_PATCHES/BUILD_DEVICE --output PATH_TO_PREVIOUS_PATCH OTA_RSR
ssh
ipsw ssh command allows us to configure debugserver and to dump shsh blobs. debugserver allows us to remotely debug applications, while the shsh blobs allows us to restore our iPhone to lower version using them.
debugserver
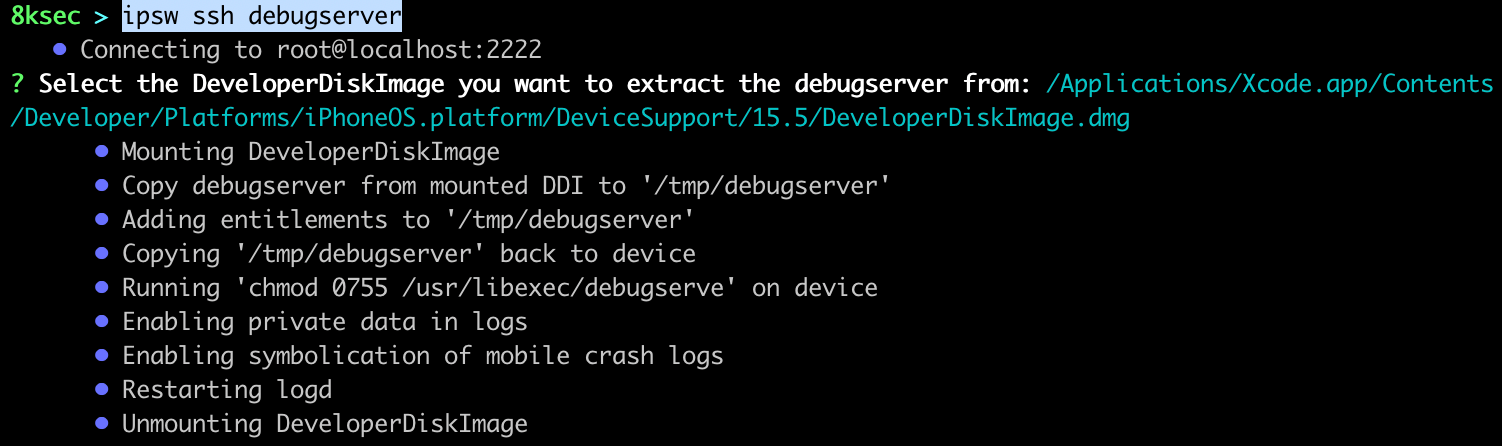
To set-up debugserver on the device, we first need to setup the proxy between us and the mobile device, we can do so using ipsw idev proxy and then we just type ipsw ssh debugserver.
command: ipsw ssh debugserver

We have come to an end of this two-part series where we have covered a lot of ipsw commands and its functionality. ipsw is indeed The Swiss Army Knife for iOS/MacOS security research as it provides a lot more and it takes a bit of time to explore all of its capabilities. Additionally, it is good source for anyone who wants to learn more about internals of different iOS/MacOS components.
GET IN TOUCH
Visit our training page if you’re interested in learning more about these techniques and developing your abilities further. Additionally, you may look through our Events page and sign up for our upcoming Public trainings.
Check out our Certifications Program and get Certified today.
Please don’t hesitate to reach out to us through out Contact Us page or through the Button below if you have any questions or need assistance with Penetration Testing or any other Security-related Services. We will answer in a timely manner within 1 business day.
We are always looking for talented people to join our team. Visit out Careers page to look at the available roles. We would love to hear from you.