Why you should remove SSL Pinning from Your Mobile Apps in 2025
Introduction
SSL pinning, or certificate pinning, is a security technique used in mobile and web applications to prevent machine-in-the-middle (MITM) attacks by restricting which certificates the app trusts. Instead of relying on the standard Certificate Authorities (CAs) for authentication, the app stores a predefined certificate or public key and only accepts connections that match the pinned certificate.
This technique was widely adopted to enhance security, ensuring that users connect only to a trusted server, even if a rogue CA issues a fraudulent certificate. However, while the intention behind SSL pinning is good, it comes with significant risks and maintenance challenges. In the security industry, SSL pinning is often recommended as a best practice, but in reality, it is an illusion of security. It creates more issues than it solves and can easily be bypassed by attackers.
The Risks of SSL Pinning
While SSL pinning was initially seen as an extra security layer, it now introduces more problems than benefits, especially as security practices evolve. Here are some of the critical risks of using SSL pinning in 2025:
1. Service Disruptions Due to Certificate Changes
One of the biggest downsides of SSL pinning is that if the pinned certificate changes due to certificate renewal, revocation, or CA migration, the application will stop working until a new version of the app with an updated certificate is released. All Users must upgrade to this latest version to use the app properly. This means:
- Apps can break suddenly, leading to downtime.
- The only fix is pushing a new app update, which takes time and depends on user adoption.
- Critical services can become unavailable, impacting user experience and business operations.
2. Industry Leaders Now Advise Against SSL Pinning
- Industry Leaders like Google now recommend not enabling SSL pinning in mobile and web applications. Google advises against pinning in its Android security best practices, emphasizing that relying on the default CA trust model is a more sustainable and secure approach. Similarly, Cloudflare discourages SSL pinning, stating that it increases operational risks and does not provide significant security benefits compared to alternative security mechanisms.
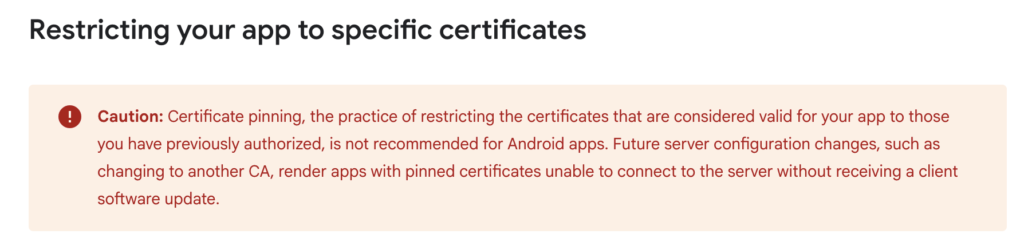 Reference: https://developer.android.com/privacy-and-security/security-ssl
Reference: https://developer.android.com/privacy-and-security/security-ssl
3. SSL Pinning is Easily Bypassed
-
Despite its intent to increase security, SSL pinning can be bypassed using tools like:
-
Frida – A powerful dynamic instrumentation toolkit that allows bypassing SSL pinning in real-time.
-
Xposed Framework Modules – Enables disabling SSL pinning on rooted devices.
-
Attackers who truly want to bypass SSL pinning can do so with these tools, making SSL pinning more of an inconvenience for developers than a robust security measure. This further proves that SSL pinning gives a false sense of security rather than actual protection.
Better Alternatives to SSL Pinning
Given the challenges and evolving security recommendations, here are some better ways to secure your app’s communication in 2025:
1. Detecting Proxies and Debugging Tools
Instead of SSL pinning, monitor the device environment to detect security risks:
- Check for active proxies, VPNs, or MITM tools like Burp Suite.
- Detect rooted/jailbroken devices where attackers can easily modify app behavior.
- Monitor runtime manipulation attempts using tools like Frida detection.
Collect this Data on the Server Side to make an informed decision.
2. Leverage Device-Fingerprinting Techniques and Anomaly Detection
Instead of blindly trusting SSL pinning, implement real-time API request monitoring to detect anomalies such as:
- Unexpected geolocation access.
- Suspicious API request patterns.
- Token misuse or replay attacks.
- Use anti-fraud mechanisms and device fingerprinting techniques to track suspicious behavior, identify compromised devices, and prevent unauthorized access.
Several vendors offer device fingerprinting solutions that detect VPNs, Frida, jailbroken devices, and more, all packaged within an SDK to help make informed security decisions.
Always make the ultimate decision to block or allow requests on the backend, not the frontend. One of the main issues with SSL pinning is that it enforces request blocking on the client side, which leads to significant reliability and security challenges.
Conclusion: Time to Move On from SSL Pinning
In 2025, the risks of SSL pinning far outweigh its benefits. With industry leaders advising against it, certificate authorities evolving, and modern security measures providing better protection, it’s time for developers to move away from SSL pinning. Instead, focus on proxy detection, Device Fingerprinting, API security, and runtime security monitoring to safeguard your application effectively.
By adopting these alternative approaches, you can ensure that your app remains secure without the risk of breaking due to certificate changes. Security should be about adaptability, not rigidity, and removing SSL pinning is a step in the right direction.
The next time a pentester reports SSL Pinning as a valid security issue, challenge it by highlighting its bypassability, industry deprecation, and the illusion of security it creates rather than providing real protection.
Explore Our On-Demand Courses
If you’re interested in diving deeper into topics like this, 8ksec Academy offers a wide range of on-demand courses tailored for security professionals and enthusiasts.
Visit academy.8ksec.io to explore our full catalog of courses. Whether you’re a beginner or an experienced professional, you’ll find resources to enhance your skills and stay ahead in the fast-evolving field of Mobile Security.
Feel free to reach out to us at support@ to ask any questions related to our blogs or any future blogs that you would like to see.
Have a great day !



