Mobile Malware Analysis Part 4 – Intro to iOS Malware Detection
All parts in this series
- 1 Mobile Malware Analysis Part 1 - Leveraging Accessibility Features to Steal Crypto Wallet
- 2 Mobile Malware Analysis Part 2 - MasterFred
- 3 Mobile Malware Analysis Part 3 - Pegasus
- 4 Mobile Malware Analysis Part 4 – Intro to iOS Malware Detection
- 5 Mobile Malware Analysis Part 5 – Analyzing an Infected Device
- 6 Mobile Malware Analysis Part 6 - Xenomorph
- 7 Mobile Malware Analysis Part 7 - Blackrock
- 8 Mobile Malware Analysis Part 8 - deVixor
Welcome to Part 4 of the Mobile Malware Series. In this part we will cover what is iOS malware, its types, methods of gathering forensics information, as well as, taking a look at some interesting system files from the forensics perspective.
In the last couple of years iOS has became an interesting target for malware developers. iPhones generally have a lot of security measures built-in, and because of that they are an interesting target for malware developers. Additionally, a lot of high value individuals are using iPhones so it makes sense from the malware developers point of view to target them. Just like any other device, iPhones are not without flaws and it has been shown again and again that threat actors can indeed compromise the device and get what they want whether it is just for the purpose of stealing user information, surveillance or something else.
Some of the iOS malware types are:
- Adware - abusing the device to get ads revenue
- RAT - Remote Access Trojan allows the threat actors to remotely control the device
- Spyware - stealing users information and this is the most common one
Filesystem dump
As usual with forensics, we need to do the filesystem dump or to create an image for it. We can do the same with iOS device, but the device needs to be jailbroken so in a lot of times, this can’t be accomplished and we need to obtain information using other methods.
iTunes Backup
If we cannot obtain the image of the device, we should be taking a look at the backups of the device. For that, we can use tools such as idevicebackup2 to create one. When we are crating the backup with the idevicebackup2, we have an option to create encrypted or non-encrypted backup. Encrypted backups provide a lot more coverage and useful artefacts so in forensics situations, we should use them.
Sysdiagnose
Sysdiagnose is a utility on most macOS and iOS devices that can be used to gather system-wide diagnostic information. It provides a lot of useful information for forensic investigators, such as running process, installed application and so on.
Some useful information from sysdiagnose includes:
- Processes
- Network Info
- Accounts info
- AirDrop logs
To dump the sysdiagnose logs, on macOS we can just execute sysdiagnose as root user.
To dump the sysdiagnose on iOS, we hold the combination of keys (holding together Volume Up and Down button along with the Power button) on the iPhone and after a couple of minutes we can download the archive from the Settings -> Privacy & Security -> Analytics & Improvements -> Analytics Data
After extracting the archive, we can examine the files inside of there and search for forensics artifacts.
Each of these three methods have their own pros and cons. For example, we can use filesystem dump when we have an access to the jailbroken device, but we could distort some evidences in the process. Backups provide only subset of files from the device which can sometimes be enough to detect some artifacts. Sysdiagnose is the easiest and quickest to get but it provides a smaller amount of files from device than the backup or filesystem dump. Indicators of Compromise (IOCs)
Before we go any further we need to define a couple of things, the first being Indicators of Compromise. Indicators Of Compromise are a bits of data which uniquely identifies the specific piece of malware.
They can be things such as:
- File traces
- Suspicious processes and URLs
- Binary Hashes
- Network Traffic
- Provisioning profiles
- Trusted certifications
IOCs enable professionals to detect intrusion attempts or other malicious activities. They are also useful when shared with the community so that they can improve their incident response.
To assist and generalise the idea of IOCs, STIX project was created.
STIX Framework and TAXII
STIX Framework
Structured Thread Information Expression (STIX) is a structured language for describing cyber threat information so it can be shared, stored, and analyzed in a consistent manner. STIX framework enhances the capabilities of organisation do defend against cyberattacks.
STIX framework is based on the indicators and the objects such as hash, IP addresses, malware, etc.
Below is an example of the hash indicator and its malware object:
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--71312c48-925d-44b7-b10e-c11086995358",
"created": "2017-02-06T09:13:07.243000Z",
"modified": "2017-02-06T09:13:07.243000Z",
"name": "CryptoLocker Hash",
"description": "This file is a part of CryptoLocker",
"pattern": "[file:hashes.'SHA-256' = '46afeb295883a5efd6639d4197eb18bcba3bff49125b810ca4b9509b9ce4dfbf']",
"pattern_type": "stix",
"indicator_types": ["malicious-activity"],
"valid_from": "2017-01-01T09:00:00.000000Z"
}{
"type": "malware",
"id": "malware--81be4588-96a8-4de2-9938-9e16130ce7e6",
"spec_version": "2.1",
"created": "2017-02-06T09:26:21.647000Z",
"modified": "2017-02-06T09:26:21.647000Z",
"name": "CryptoLocker",
"description": "CryptoLocker is known to hold files hostage for ransom.",
"malware_types": ["ransomware"]
}Indicator has a lot of fields, but the most interesting ones are name, description, pattern and indicator_types. Name and description are self-explanatory, pattern tells what is the pattern to match it, such as hash in the example above, while the indicator_types describe this pattern of SHA256 of the file as malicious activity.
Malware object contains information about the file which has a SHA256 identified as CryptoLocker such as name, description and malware type.
Following is an excerpt from the mvt-indicators repo for Operation Triangulation.
"objects": [
{
"type": "malware",
"spec_version": "2.1",
"id": "malware--01e5af02-75fd-44f4-890a-d3b6efee9c64",
"created": "2023-10-23T15:49:48.089255Z",
"modified": "2023-10-23T15:49:48.089255Z",
"name": "OperationTriangulation",
"description": "IOCs related to Operation Triangulation iOS spyware documented by Kaspersky Labs.",
"is_family": false
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--c5788b5b-128f-43f2-b5f5-02f8055d4700",
"created": "2023-10-23T15:49:48.089417Z",
"modified": "2023-10-23T15:49:48.089417Z",
"indicator_types": [
"malicious-activity"
],
"pattern": "[domain-name:value='senlin83.com']",
"pattern_type": "stix",
"pattern_version": "2.1",
"valid_from": "2023-10-23T15:49:48.089417Z"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--52da4e9a-3a22-4681-94db-e7ce3ec5b6d5",
"created": "2023-10-23T15:49:48.09267Z",
"modified": "2023-10-23T15:49:48.09267Z",
"relationship_type": "indicates",
"source_ref": "indicator--c5788b5b-128f-43f2-b5f5-02f8055d4700",
"target_ref": "malware--01e5af02-75fd-44f4-890a-d3b6efee9c64"
},
{
"type": "indicator",
"spec_version": "2.1",
"id": "indicator--90a3e899-c7b8-480f-842f-86baf929a3b8",
"created": "2023-10-23T15:49:48.093005Z",
"modified": "2023-10-23T15:49:48.093005Z",
"indicator_types": [
"malicious-activity"
],
"pattern": "[domain-name:value='backuprabbit.com']",
"pattern_type": "stix",
"pattern_version": "2.1",
"valid_from": "2023-10-23T15:49:48.093005Z"
},
{
"type": "relationship",
"spec_version": "2.1",
"id": "relationship--824ac4a8-9fd3-4909-94ea-5f25a2665829",
"created": "2023-10-23T15:49:48.093516Z",
"modified": "2023-10-23T15:49:48.093516Z",
"relationship_type": "indicates",
"source_ref": "indicator--90a3e899-c7b8-480f-842f-86baf929a3b8",
"target_ref": "malware--01e5af02-75fd-44f4-890a-d3b6efee9c64"
}
...The first object is a malware which contains the name and description which marks it as OperationTriangulation malware. The second object is indicator which is marked as malware-activities and the pattern for it is that the domain name is senlin83.com. The third object is a relationship object which binds together these two (malware and indicator), meaning that the indicator with domain name snlin83.com indicates the malware OperationTriangulation. Following that, we can see another indicator which just like the first indicator contains the domain name backuprabbit.com. Finally, we have another relationship which combines together the previous indicator and the malware and indicates that the indicator with domain name backuprabbit.com indicates OperationTriangulation malware.
STIX is an extensive framework and it takes a bit time to get familiar with it. STIX is designed to be shared via TAXII.
TAXII
Trusted Automated Exchange of Intelligence Information (TAXII) is an application protocol for exchanging CTI (Cyber Thread Intelligence) over HTTPS. It is a protocol that allows sharing STIX files between organisations.
Even though, the STIX and TAXII are independent frameworks, when used together they form a powerful framework for sharing and using threat intelligence.
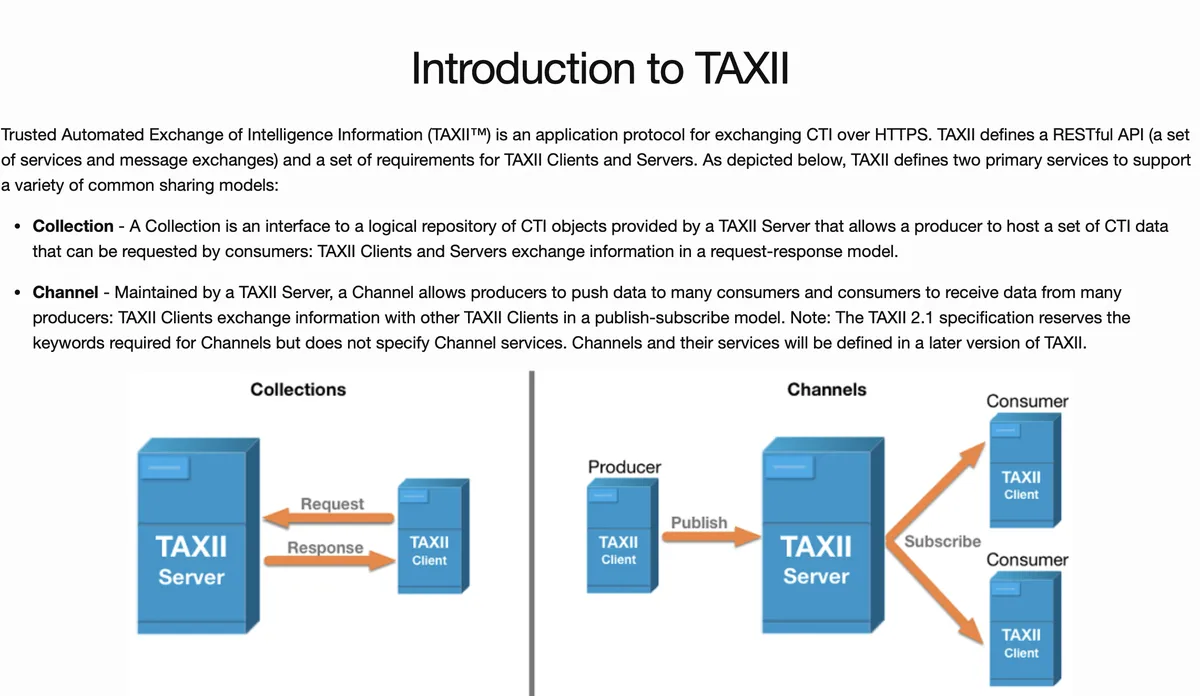
Main two concepts in TAXII are the collection and the channel. A collection is a set of STIX packages organised and managed by the single entity, such as a security vendor or a government agency. A channel allows organizations to access a specific collection, such as through API, file exchange, or threat intelligence platform. A channel allows user to push data to multiple consumers.
Using STIX and TAXII can improve the threat intelligence sharing as it provides the common language for the organizations to share and exchange threat intelligence and because the data is in the standard format it can improve threat detection and response. Additionally, using STIX/TAXII ensures that the intelligence data is consistent and accurate.
Indicators Of Compromise Repositories
Good thing to do is to take a look at indicators of compromise for malware. This can prove a valuable learning lesson as we can see what are some traces that the malware leaves behind and what should we search for.
We have a couple option from where we can download and view IOCs, such as:
- https://github.com/mvt-project/mvt-indicators - indicators from mvt
- https://github.com/AssoEchap/stalkerware-indicators - indicators of different Stalkerwares
- https://github.com/AmnestyTech/investigations - indicators from Amnesty International which has created mvt
Analysing backup or a filesystem dump
After we have obtained either an image or the backup, we need to analyse it. To analyse the backup, we can use tools such as mvt created by the Amnesty International Security Lab or analysing files manually by using tools such as the ones provided inside of libimobiledevice.
Mobile Verification Toolkit allows us to extract artifacts from either filesystem dump or iTunes backup, decrypting backup or checking Indicators Of Compromise (IOC).
Mobile Verification Toolkit is a collection of utilities designed for the purpose of identifying any signs of compromise.
Key features of the mvt are:
- Decrypting encrypted backups
- Processing and parsing records from numerous iOS system and apps databases, logs and system analytics
- Compare extracted records to malicious indicators in STIX2 format
- Generating JSON logs of extracted records and JSON logs of all detected malicious traces
- Generating a unified chronological timeline of extracted records
Interesting files on iOS
A lot of files exists on iOS that are useful for iOS forensics. Some of them are:databases in /private/var/Keychains/Analytics/ - data about networking, certificate pinning, TLS, etcCalendar.sqlitedb may contain interesting mail addressesCallHistory.storedata contains information of incoming and outgoing calls, including messaging applications such as WhatsAppcom.apple.identityservices.idstatuscache.plist - contains cache of Apple user ID authentications which may be useful to get information when apps such as iMessage first established contacts with other registered Apple IDsAddressBook.sqlitedb - contains information about the phone’s address bookShortcuts.sqlite - contains records about the Shortcuts application; can be useful because app may be abused by spyware to obtain persistencecom.apple.osanalytics.addaily.plist - contains history of data usage by processes which is useful to gain traces of malicious process executions and relevant timeframesDataUsage.sqlite - contains information about the network usage by processes. This database does not log WiFi connectionsnetusage.sqlite - like the previous two instances, this one also contains data usage by processesBrowserState.db - contains record of opened tabs in Safari/private/var/mobile/Library/Image Cache/Favicons/Favicons.db or /private/var/mobile/Containers/Data/Application//Library/Image Cache/Favicons/Favicons.db - contains mapping between Favicons URLs and the URLs which loaded them/private/var/mobile/Library/Safari/History.db or /private/var/mobile/Containers/Data/Application//Library/Safari/History.db - contains history of visited URL by Safarisms.db - contains SMS messagesTCC.db - contains information about TCC (which apps have which services, such as microphone, camera, etc.)
History
Uygures campaign
In 2019, Google Project Zero revealed a chain of exploits that lead to the compromise of iOS devices from version 10 all the way to 12 and the initial entry point exploits were browser exploits (Safari). You can read full analysis on the Google Project Zero post (https://googleprojectzero.blogspot.com/2019/08/a-very-deep-dive-into-ios-exploit.html)
Pegasus V2
In 2021, Citizen Lab has revealed how FORCEDENTRY (CVE-2021-30860) vulnerability was used to exploit the device and deliver Pegasus. Pegasus is a spyware developed by the NSO. The FORCEDENTRY was zero-click exploit against iMessage. The vulnerability was present in parsing of GIF images. More information is available in the post of Citizen Lab (https://citizenlab.ca/2021/09/forcedentry-nso-group-imessage-zero-click-exploit-captured-in-the-wild/) and analysis on the Google Project Zero (https://googleprojectzero.blogspot.com/2021/12/a-deep-dive-into-nso-zero-click.html).
Hermit
In 2022, Google Project Zero wrote about CVE-2021-30983 which was a fake carrier application. It contained six different privilege escalation exploits, five of these were well-known exploits for older versions of iOS, while the sixth one was related to the DCP (Display Co-Processor) which contains most of the display drivers. All iPhones above iPhone 12, including it, as well as, all M1 are using DCP.
Reign
In 2023, Citizen Lab wrote about ENDOFDAYS exploit which was used to deliver QuaDream’s spyware known as Reign. QuaDreams is an Israeli company which is similar to NSO company in the way they operate. The entry point was obtained by abusing XML parsing of data inside of database for iCloud calendar. More information about this is available https://citizenlab.ca/2023/04/spyware-vendor-quadream-exploits-victims-customers/
Pegasus V3
In 2023, Citizen Lab revealed yet another instance of Pegasus which was using PWNYOURHOME exploit. PWNYOURHOME exploit was two-step zero-click exploit which targets HomeKit in the first step and iMessage in the second step. This exploit was used against iOS 15 and 16. Additionally, they have identified FINDMYPWN exploit which was deployed against iOS 15 in which the first step targets Find My feature, while the second one targets iMessage like PWNYOURHOME. More information about PWNYOURHOME and FINDMYPWN can be seen on the Citizen Lab post (https://citizenlab.ca/2023/04/nso-groups-pegasus-spyware-returns-in-2022/).
Operation Triangulation
In 2023, Kaspersky wrote about Operation Triangulation. Like a couple of previous exploits, this one was exploiting iMessage. It also prevents the iOS updates to happen.
Pegasus V4
In September of 2023, Citizen Lab has written a post about BLASTPASS exploit which was targeting latest iOS at time (16.6) without any user interaction. The exploit was abusing parsing attachments inside of PassKit. BLASTPASS is described in Citizen Lab post (https://citizenlab.ca/2023/09/blastpass-nso-group-iphone-zero-click-zero-day-exploit-captured-in-the-wild/).
Attack surfaces
As we can see, attack surfaces differentiate a lot. We can see that the known exploits were mostly targeting iMessage and HomeKit. However, other methods were abused such as PassKit in the BLASTPASS, Find My feature in Pegasus and Safari exploits in Uygures campaign.
Downloading samples
Sometimes it is not possible to extract or we can get only minimum amount of artifacts due to the malware cleaning-up their tracks. For example, in the case of ENDOFDAYS malware deletes the events from the calendar which was the entry point to the system. We can download malware samples to learn and analyze malware from places such as Malware Bazaar and vx-underground.
Conclusion
This marks the end of the first blog about the iOS malware detection. We have learned the different methods of obtaining forensics artefacts, such as filesystem dump, backup as well as sysdiagnose and their pros and cons. Additionally, we went briefly over the STIX and TAXII frameworks and what is their power. We have covered Indicators of Compromise and some places where we can find them along with some useful iOS files.
In the next blog post we will practically inject malware into the device and analyze it.
GET IN TOUCH
Visit our training page if you’re interested in learning more about these techniques and developing your abilities further. Additionally, you may look through our Events page and sign up for our upcoming Public trainings.
Check out our Certifications Program and get Certified today.
Please don’t hesitate to reach out to us through out Contact Us page or through the Button below if you have any questions or need assistance with Penetration Testing or any other Security-related Services. We will answer in a timely manner within 1 business day.
We are always looking for talented people to join our team. Visit out Careers page to look at the available roles. We would love to hear from you.



