Hacking Android Games
Table of contents:
a. Android Game Hacking Introduction and prerequisites
b. General introduction to game hacking
c. Reverse engineering Unity games
1-Android Game Hacking:
Greetings and welcome to our blog post on the topic of Android game hacking. Today, we aim to provide you with an overview of the process involved in hacking Android games. It’s crucial to distinguish between app hacking and game hacking within the Android ecosystem. While games are a form of application, the methodologies employed to hack them differ from the standard OWASP top 10 for mobile applications.
An important point is that most games on the Android platform are developed using Unity. Consequently, it’s pertinent to understand about Unity game hacking, given that most game developers utilize game engines rather than building games from scratch. Before we proceed, let’s outline the prerequisites:
- il2cppdumper (https://github.com/Perfare/Il2CppDumper)
- frida-il2cpp-bridge (https://github.com/vfsfitvnm/frida-il2cpp-bridge)
- Frida
- Dnspy (https://github.com/dnSpy/dnSpy)
Objective: Increase your money in Dude Theft Wars Shooting Android Game
Version =0.9.0.9a
Google Play Store Link : https://play.google.com/store/apps/details?id=com.PoxelStudios.DudeTheftAuto&hl=en&gl=US
The Version We Tested On: https://www.apkmirror.com/apk/poxel-studios-games/dude-theft-wars-online-fps-sandbox-simulator-beta/dude-theft-wars-online-fps-sandbox-simulator-beta-0-9-0-9a-release/#downloads
2-General Introduction to Game Hacking (Optional):
If you were around before laptops and modern computing took over, chances are you remember the days of desktop PCs. Back then, games like Medal of Honor and Counterstrike were popular. Interestingly, many game developers didn’t prioritize security for their games, nor did they anticipate hacking attempts. However, they were proven wrong.
The primary method of hacking these games, and the most commonly used, involves manipulating memory. Here’s how it works:
-
Static Method (Patching):
-
Open the game in a disassembler.
-
Look for keywords like “gold,” “health,” “damage,” and “weapons”
-
Modify these values according to your preferences.
-
Close the game, sometimes needing to recompile it.
- Dynamic Method (Hooking):
- Use a program like Cheat Engine.
- Connect Cheat Engine to the game.
- Like the static method, search for keywords or values of interest.
- Change the values to whatever you want.
- Close the program.
The dynamic approach is considered more reliable and enjoyable. The static method faces hurdles, with ASLR being a prominent one. Spending hours searching for a variable only to find its address changed when the game starts can be frustrating. That’s why our focus in this blog post will be on dynamic hacking.
3-Reverse Engineering Unity games
Unity games face a significant issue that facilitates the extraction of the game’s exact source code. This issue stems from the il2cpp scripting back end framework used in Unity games. Essentially, this framework allows for the easy extraction of the original il2cpp file, which contains DLLs like Assembly-Csharp.dll, constituting the game’s actual source code. The process of extracting the source code is generally quite reliable. However, to perform this extraction, two files need to be located:
1. Global-metadata.dat
2. [Il2cpp.so](http://il2cpp.so/)
In recent years, game developers have become more vigilant, often removing the il2cpp.so file from the APK to prevent easy reverse engineering. Nonetheless, numerous workarounds exist for this issue. Sometimes, developers encrypt the metadata file to prevent dumping, although solutions to this problem also exist. For those interested, detailed research on this topic can be found at: https://katyscode.wordpress.com/2021/02/23/il2cpp-finding-obfuscated-global-metadata/.
The process of extracting the il2cpp.so file and the source code, as outlined in the blog, relies on a Frida plugin named il2cpp-bridge.
3.1-Dumping the il2cpp.so file:
In order to dump the source code, there are 2 files that we need Global metadata file and il2cpp.so native library. Don’t worry if you can’t find those in an APK,you can still dump the source code using other ways. However, let’s focus on most cases where you can find them. You can find the global metadata file in the following path “assetsbinDataManagedMetadata” and the il2cpp in the path “libarm “. If you were lucky and you found both files, go to the first method here. If you didn’t, go to the 2nd method.
Method 1: il2cppdumper program:
Download the il2cppdumper from the official GitHub page, then open the executable program. You will see a window opening to browse for files:
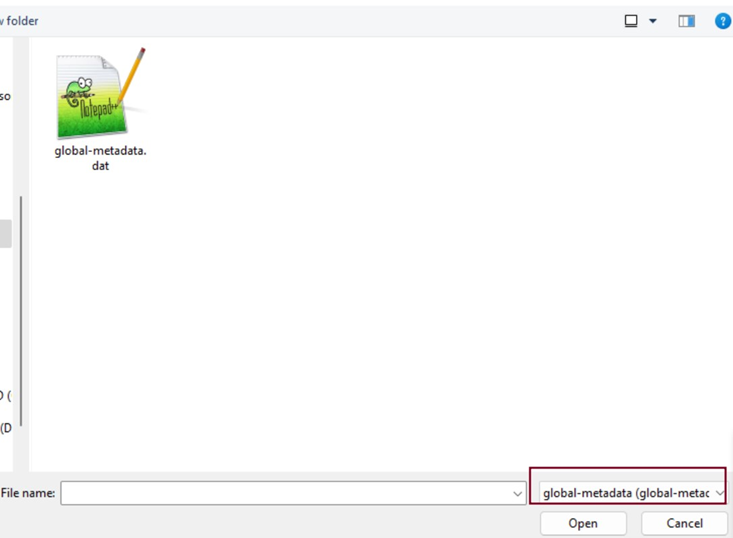 Figure 1 Global Metadata File
Figure 1 Global Metadata File
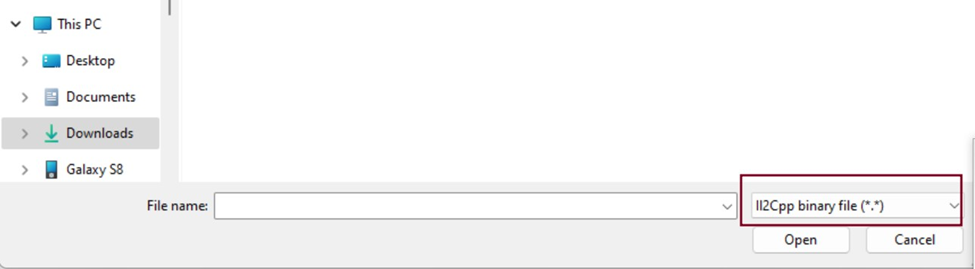 Figure 2 Ill2cpp Binary File
Figure 2 Ill2cpp Binary File
After that wait for magic to happen and the program to dump the source code as seen below:
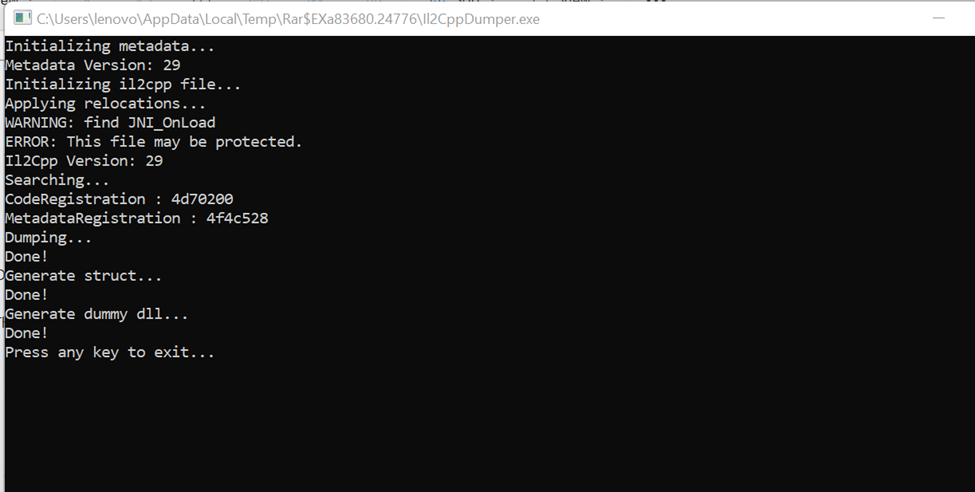 Figure 3 Dump Source Code
Figure 3 Dump Source Code
You can find a folder named “DummyDLL” in the path the Il2cppdumper exists. If you find dumped dlls there, then move to the next section about static analysis using Dnspy.
What if the il2cpp.so doesn’t exist?
In case you couldn’t find the il2cpp.so file as seen in the below rar file, there is one more trick that could really help you.
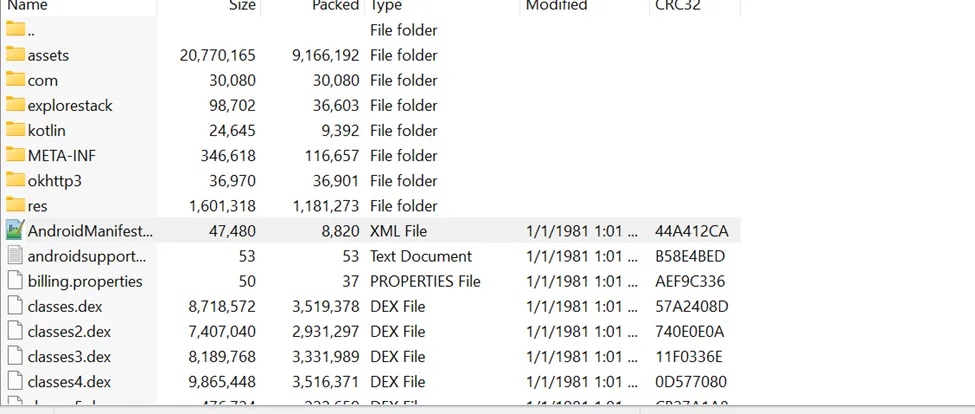 Figure 4 No Il2cpp.so
Figure 4 No Il2cpp.so
Open the adb shell, and go directly into the app ‘s folder, it’s highly likely that you will see the libs folder.
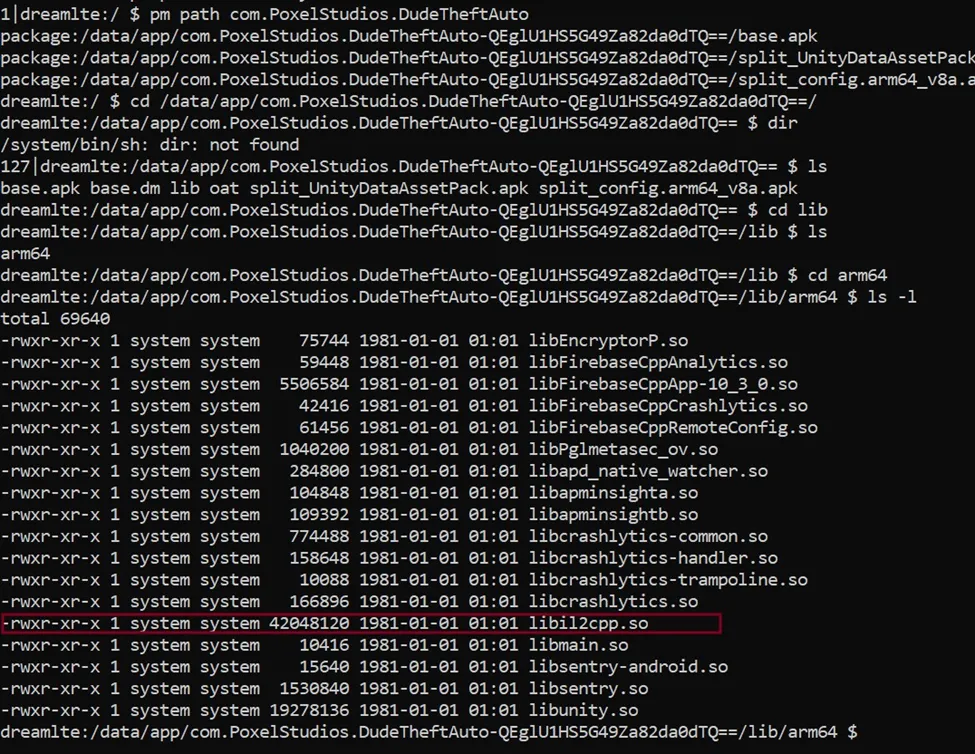 Figure 5 Native Library Found After Installation
Figure 5 Native Library Found After Installation
Method 2: il2cpp-bridge way:
Download the il2cpp-bridge plugin from the official GitHub page too. According to the official page in order[Link] to dump the il2cpp file you only need one method “Il2Cpp.dump();“. After that you will find a cs file with the method names and argument
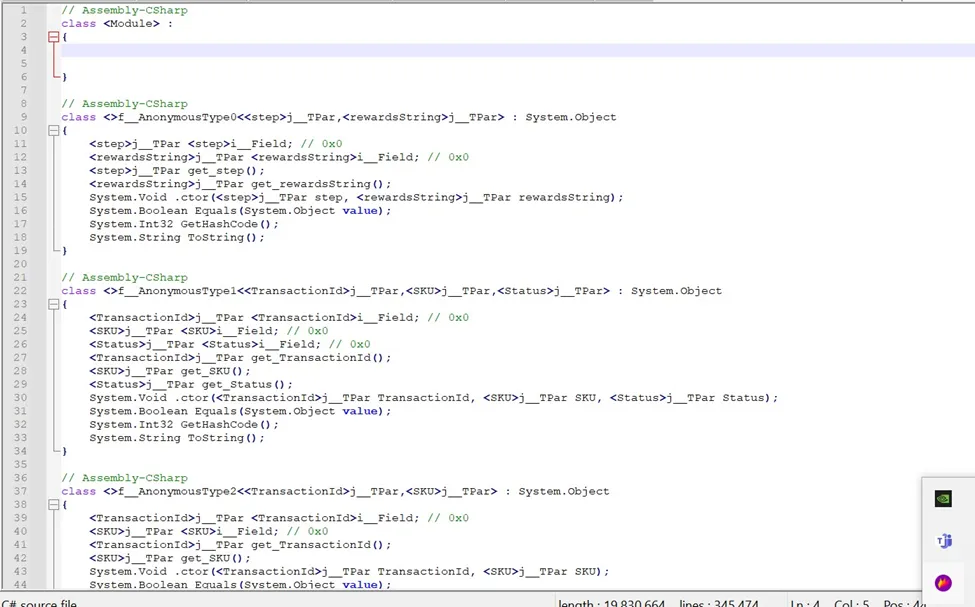 Figure 6 Dumped Source Code Using Plugin
Figure 6 Dumped Source Code Using Plugin
3.2-Static analysis using Dnspy:
Reverse engineering and reading code are an art. It’s like understanding how a building works through its blueprint and inner pipes. It’s truly amazing and fulfills the inner child ‘s curiosity in each one of us!
If you are trying to hack a game, you can try cracking the game ‘s own rules and modes. That and you can also try hacking the game itself according to the normal pentesting process. Meaning you can look for XSS,SQLI,IDORs,etc…However, since most properly games are different and implement a different ecosystem of coins,health,inventory,and other customized logic for each user, let’s start by looking for those.
Old school way of game hacking :(String search)
Our target is finding the function that updates and adds money or coins, so let’s search for methods with words that have money and coins in them, and words like “add,update,increase “. Sometimes you might want something that circumvents the logic at runtime, so look at something that deals with the keyword “money**”.
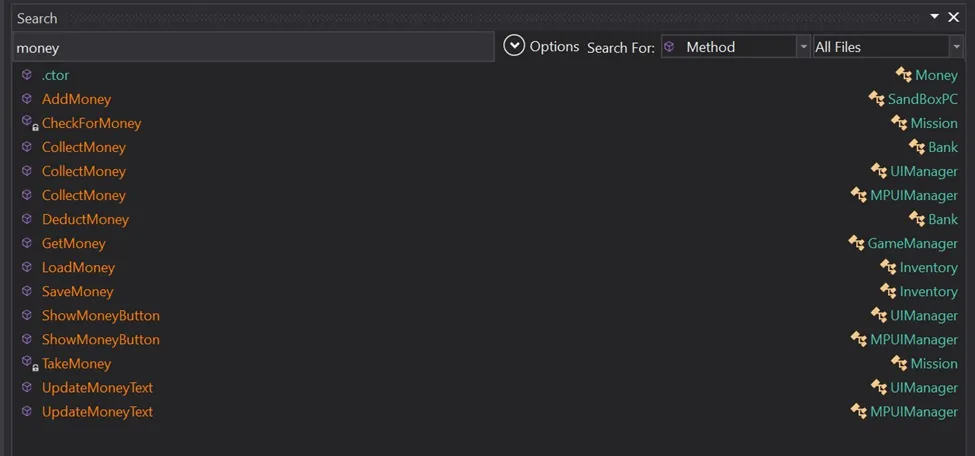 Figure 7 Searching For Interesting Functions
Figure 7 Searching For Interesting Functions
Let’s try digging deeper into the collectmoney function.
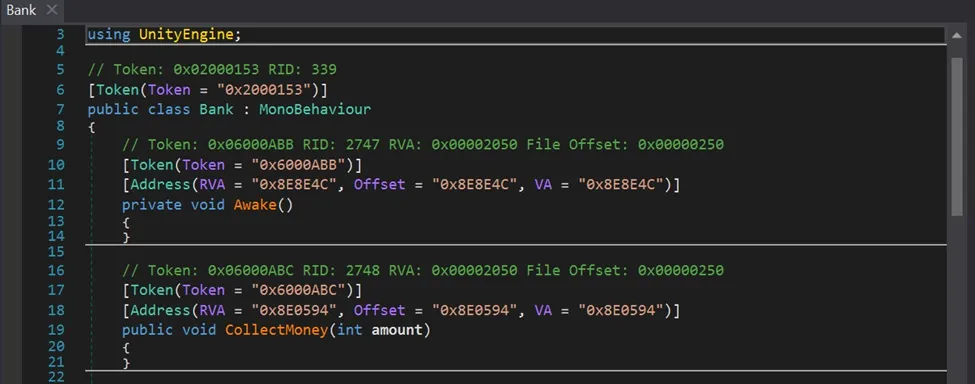 Figure 8 Collect Money Function
Figure 8 Collect Money Function
Looking at the function it looks very self-exploratory. It’s a function that takes an integer value and then adds it to the user ‘s bank account. To validate our assumption. We move on to the next phase.
In summary, what do to do during the static analysis phase?
Focus on 3 things:
- Return value of target function
- Parameters and their types
- The offset
3.3-Dynamic analysis on Android games using Frida:
Method 1: il2cppbridge
The il2cppbridge plugin is very useful and might just be the best tool to use if you have Frida and want to hack a Unity game. Below the Il2cpp.trace function is used to trace classes that we are interested in.
Il2Cpp.perform(() => {
//Il2Cpp.dump();
const Modulebase = Module.load(“libil2cpp.so”).base
const CSharp=Il2Cpp.Domain.assembly(“Assembly-CSharp”).image
const className=CSharp.class(“Bank”)})
Now the best part. Play the game while hooking the Bank class.
 Figure 9 Loading Screen For The Game
Figure 9 Loading Screen For The Game
How do we trigger the money function?
We try to find any function or action that deals with money. We see on the loading page that we can be taxi drivers to earn money, but there is a much easier way. Just throw money on the ground, then pick it up again:
 Figure 10 Dropping Money
Figure 10 Dropping Money
Notice that the total is 290$, before you pick up the money.
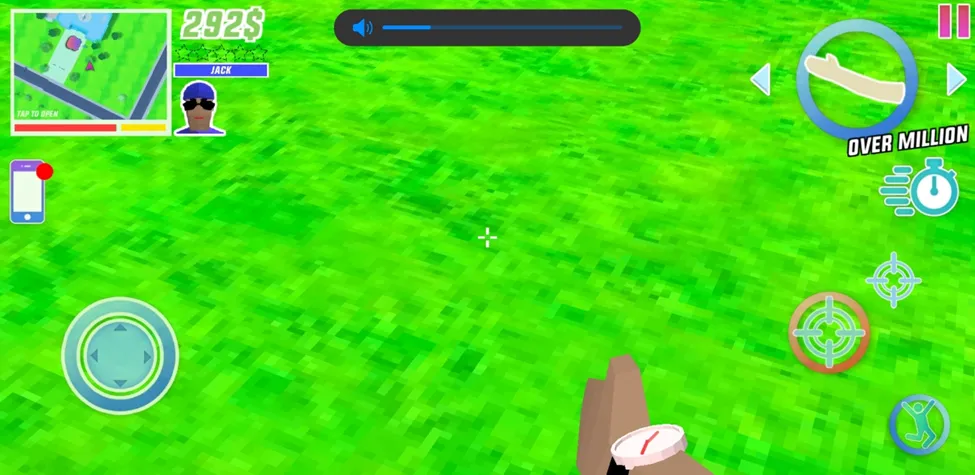 Figure 11 Collecting Money
Figure 11 Collecting Money
Now notice that the total increased 2$, the money you picked up. That is, it. Now let’s run our Frida plugin script that traces the Bank class to see if the function collectMoney is being triggered or not?
Firda Launch Command :
frida -U -f "com.PoxelStudios.DudeTheftAuto" -l _.js
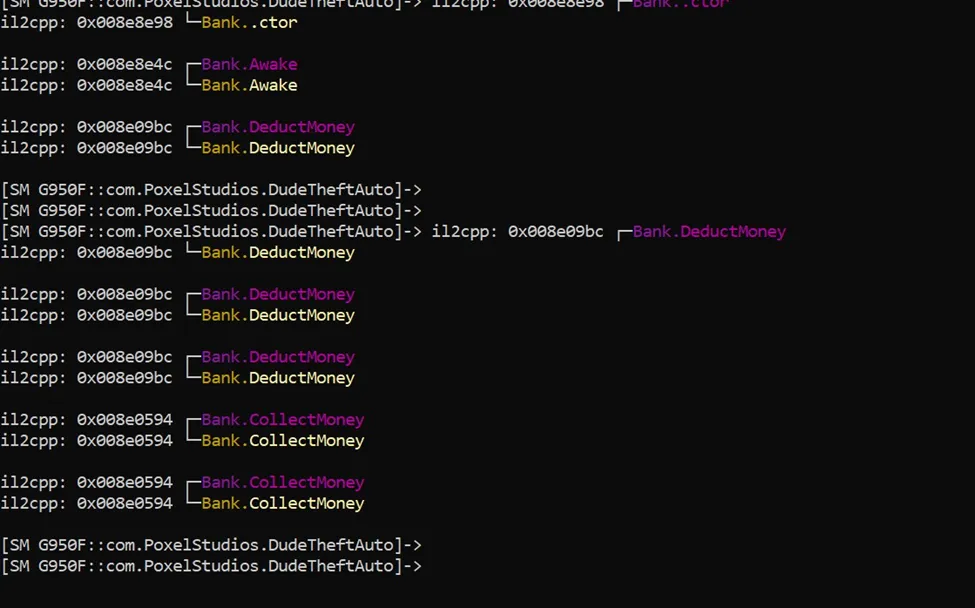 Figure 12 Tracing Bank Class
Figure 12 Tracing Bank Class
Bingoooo !!!! The first step of hacking the collectmoney function has been validated, we caught the function that deals with money collection. The next step is to use the plugin to increase the amount of money.
Let’s write a function that changes the amount of money we have to something bigger:
className.method("CollectMoney").implementation=function(arg0){
var ret=this.method("CollectMoney").invoke(arg0+2000)
return ret
}Now let’s attach our script and enjoy…
Frida –U –f com.PoxelStudios.DudeTheftAuto –l HookUnity.js
Figure 13 Dropping Money To Buy Weapon
Now notice that after we collect the money from the ground, the 2000$ is added! Figure 14 Hacking Money Increase
To confirm that the money is really changed and it’s not just a silly mistake in the UI, we try buying a weapon and we did really buy it with the fake hack money we earned Figure 15 Bought A Weapon With Hacking Money
Method 2: Frida’s interceptor
The same function could be also implemented with Frida’s interceptor:
function HookUnity(pointer,classname){
Java.performNow(function(){
Interceptor.attach(Module.findBaseAddress('libil2cpp.so').add(pointer), {
onEnter: function (args) {
console.log("[+]"+classname+" "+"is being called"+"[+]")
//console.log(args)
console.log("Intercepted integer value: " +args[1]); // Print the integer
args[1]=ptr(0x2000)
},
onLeave: function (retval) {
return retval
}
})This was just the tip of the iceberg; you can do much more with Frida. Try yourself and search for more hacks and more cool stuff to be done.
Conclusion:
Today we talked about how Unity games could be hacked using Frida in 2 ways. Unity games are known to be exploitable through hacking the il2cpp library. If you are someone who likes reading code and breaking stuff, you would enjoy doing this tutorial by hand.



