Advanced Frida Usage Part 4 - Sniffing location data from locationd in iOS
All parts in this series
- 1 Advanced Frida Usage Part 1 - iOS Encryption Libraries | 8kSec Blogs
- 2 Advanced Frida Usage Part 2 - Analyzing Signal and Telegram messages on iOS
- 3 Advanced Frida Usage Part 3 - Inspecting XPC Calls
- 4 Advanced Frida Usage Part 4 - Sniffing location data from locationd in iOS
- 6 Advanced Frida Usage Part 6 - Utilizing writers
- 7 Advanced Frida Usage Part 7 - Frida Memory Operations
- 8 Frida Advanced Usage Part 8 - Frida Memory Operations Continued
- 9 Advanced Frida Usage Part 9 - Memory Scanning in Android
- 10 Advanced Frida Usage Part 10 - Instruction Tracing using Frida Stalker
Introduction
Welcome to Part 4 of our Advanced Frida Usage series. In part three of our Frida blog posts, we went over what is XPC, how to use it, and how to intercept it with Frida.
This blog post will discuss how to use XPC tools for this job, some of them are xpcspy and gxpc. xpcspy tool is already well covered with tutorials, while the gxpc is a new tool inspired by xpcspy. It behaves the same as the xpcspy with small additions, such as recursively parsing messages (if the dictionary contain some other dictionary, it will be parsed as well), additionally it supports xpc_connection_set_event_handler which prints the address of the block implementation.
Installation
As with frida-go, gxpc supports macOS, Linux and Android. We will use macOS as a host machine. We first need to install go and download frida-core-devkit for our machine.
For our machine, we will download macos-arm64 since we are working on M1 which for the Frida version 16.0.19 is frida-core-devkit-16.0.19-macos-arm64.tar.xz.
After downloading the devkit, we will move libfrida-core.a and frida-core.h files to appropriate locations.
Now that we have everything ready, we can now run go install github.com/nsecho/gxpc@latest.
How gxpc works ?
gxpc works by using frida bindings that are written in Go using frida-go. Frida bindings enable the user to use Frida’s functionality using other languages, such as Python, Swift, node.js, Go, etc. Go has the option to interact with C code using cgo. In order to link the frida-go, we need to have frida-core dynamic libraries installed on the system as well as frida-core.h header file which is included inside the frida-core-devkit which we need to install.
Internally, gxpc traces specific xpc_* functions which we can see inside the source.js file.
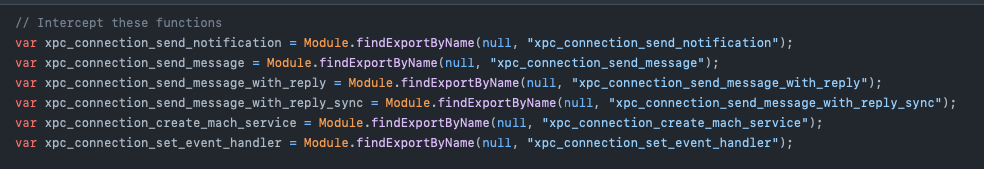
We can see the comment Intercept these functions which immediately tells us what will be done with these variables. It is using Module.findExportByName API which we have seen in previous blog posts.
It is then followed by a bunch of functions that are used to extract data out of the dictionary or array, such as xpc_dictionary_get_value or xpc_copy_description.
For each of the functions that should be intercepted, Interceptor.attach is called to intercept it. Once these functions are called, function parseAndSendDictData is called with the function name as a first parameter, xpc_connection_t as a second parameter and xpc_object_t as a third argument. parseAndSendDictData creates a JSON dictionary and extracts the data out of xpc_object_t to JavaScript objects. Once all the objects are parsed, they are added to the dictionary and sent to the Go code using send Frida’s function.
Using gxpc
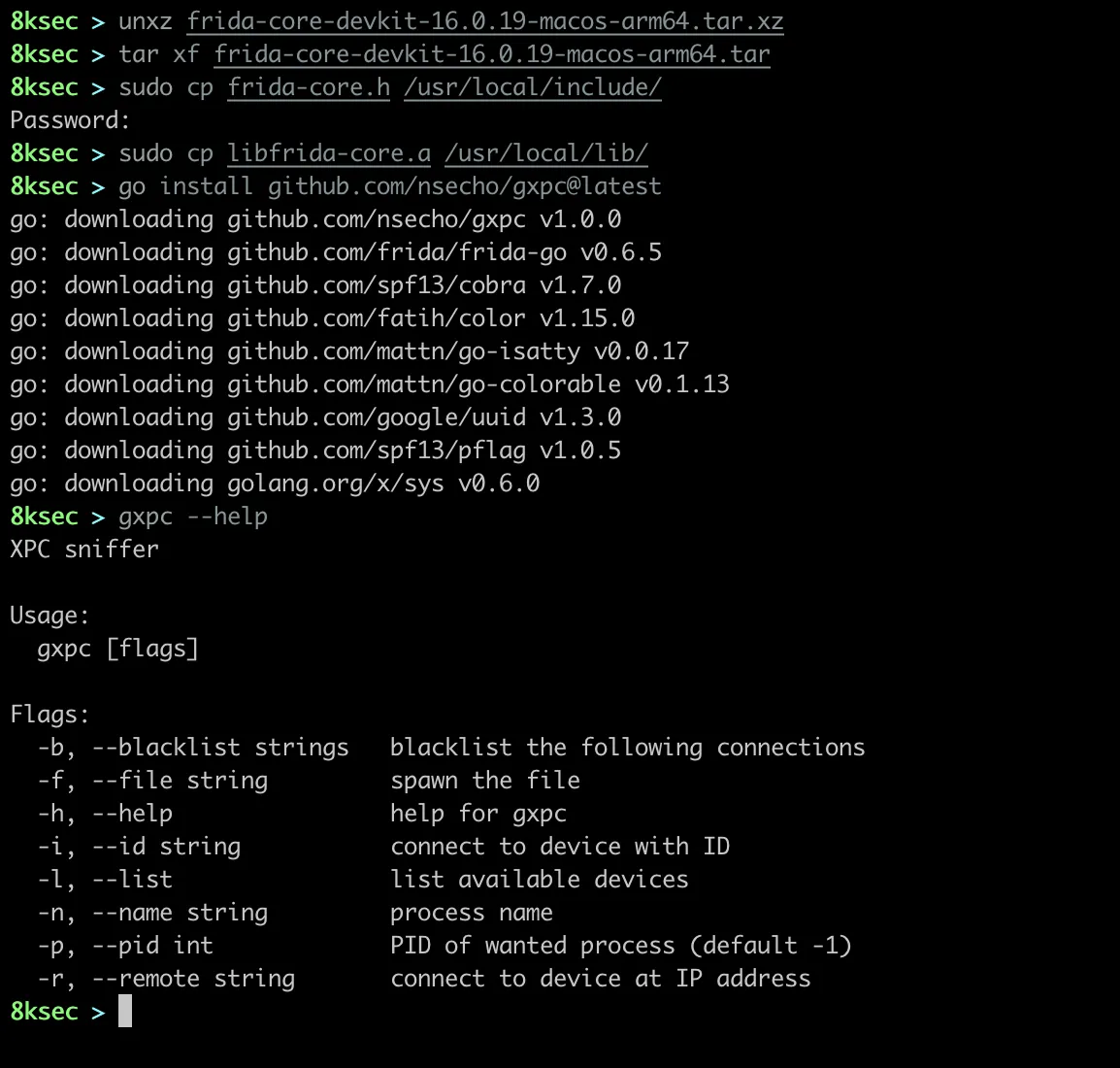
Now that we have installed gxpc** and went over how it works, let’s connect our iPhone using a USB cable, and to confirm that the device is connected we will use gxpc -l to list devices.
We can see that we have our standard local and socket devices available as well as newly connected iPhone device of type USB.
By default, gxpc will connect to the USB device if one is connected. We can also attach to the process by name(locationd, SpringBoard) or by PID. We also have an option to spawn the binary where the process is resumed once the script is loaded.
We will attach to locationd, which is the primary daemon responsible for location data. To do that, we will use gxpc -n locationd.
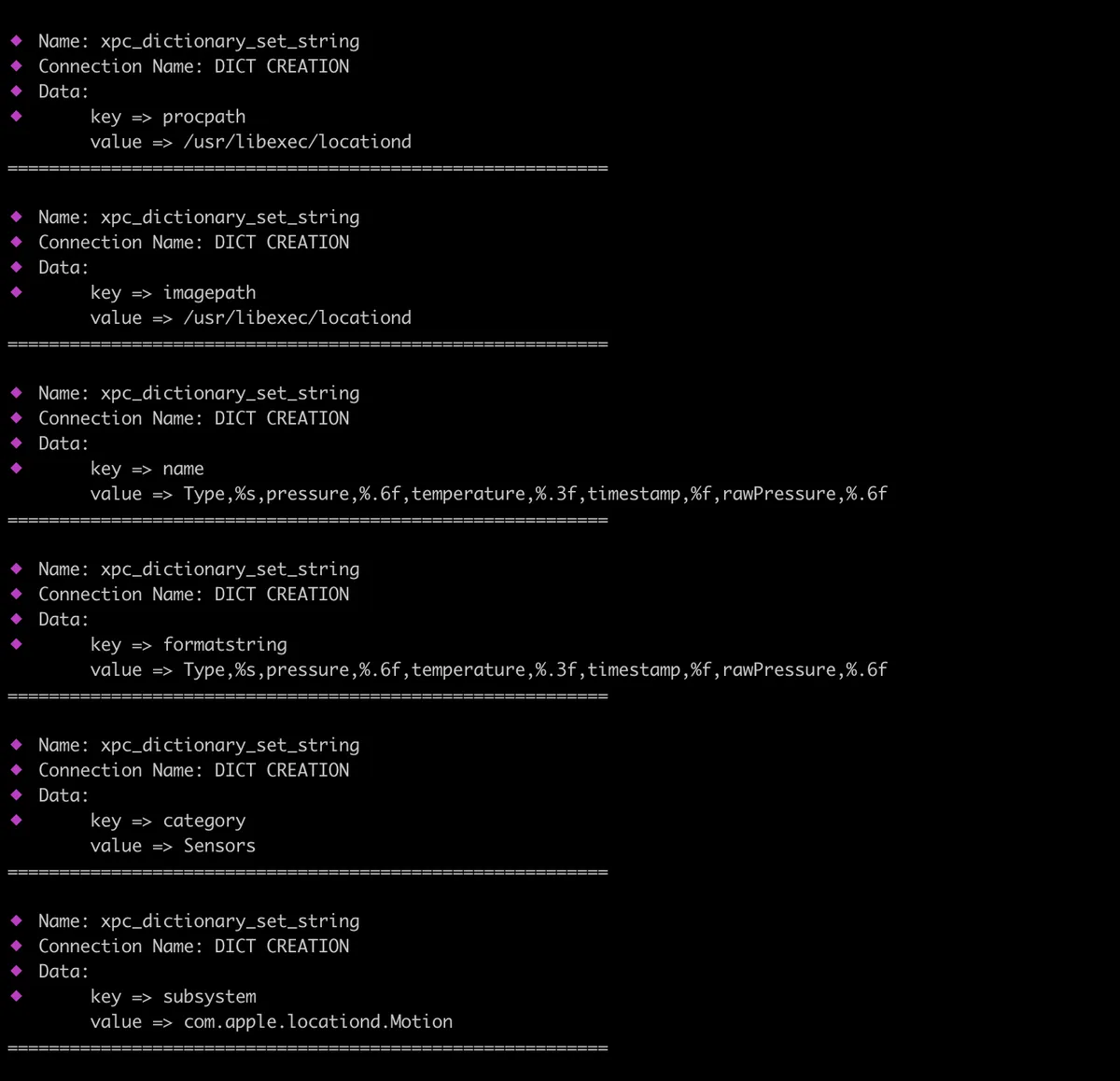
After running, we can see immediately a bunch of xpc_dictionary_set_string** functions being intercepted. We can blacklist specific connections, by using -b or —blacklist flag for gxpc. In this case, we will blacklist DICT CREATION.
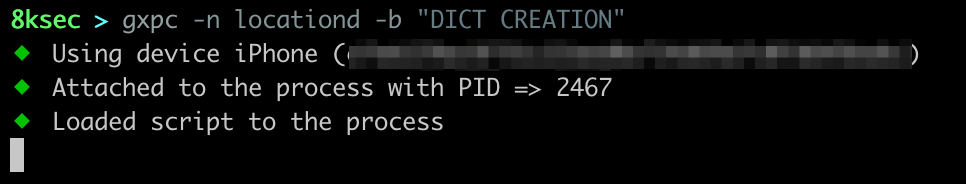
The tool will return a lot of functions being hit, to further filter on the data, let’s search in the terminal for the string longitude**.
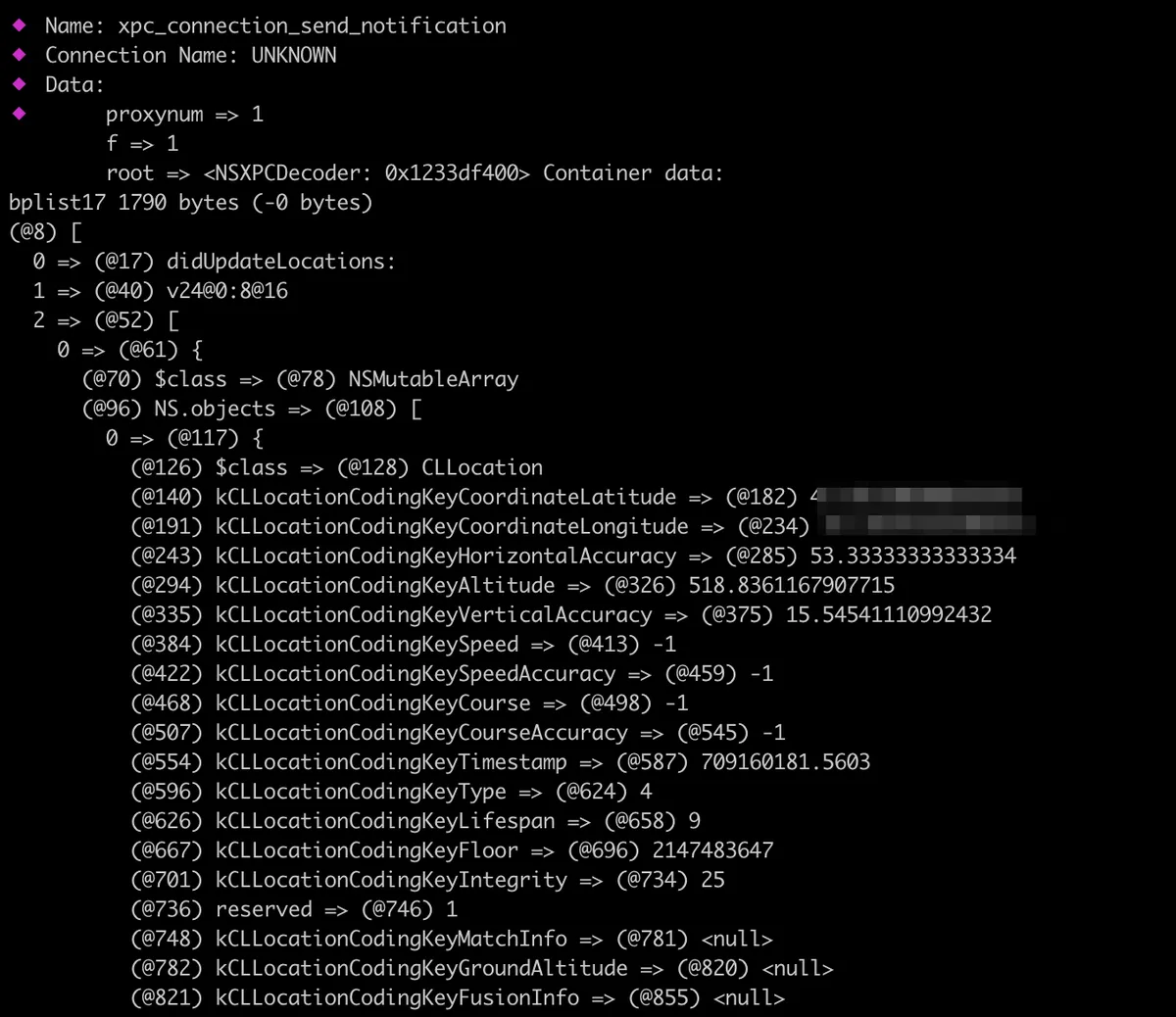
We can see that we have found the match inside the bplist17 which is sent using xpc_connection_send_notification function. The data contains a lot of useful information, such as longitude, latitude, accuracy, etc.
Now we can use the same approach to analyse different applications/binaries to analyse to which applications/daemons they are talking to and what that communication looks like. This could gives us a more opportunities to find some vulnerabilities.



